Never enough: Kaspersky has uncovered two vaccine research-related APT incidents
As the pandemic and restrictive measures continue worldwide, many stakeholders are using all available means to accelerate vaccine development. While much of the work is driven by good intentions, the coin also has another side, as some attackers try to take advantage of events for their own benefit. While Kaspersky’s experts are constantly monitoring the Lazarus Group’s campaigns targeting various sectors, they discovered that the group targeted organizations dealing with COVID-19 a few months ago. Exactly two cases were identified.
The first was an attack on a body of the Ministry of Health: on October 27, 2020, two of the organization’s Windows servers were infected with sophisticated malware. The malware called “wAgent” used in the attack is no longer unknown to Kaspersky. A more in-depth analysis showed that the wAgent malware deployed against the Department of Health had the same infection pattern as the malware the Lazarus Group had previously used in attacks on cryptocurrency companies.
The second incident involved a pharmaceutical company , which according to Kaspersky’s telemetry data was attacked on September 25, 2020. The company is developing a COVID-19 vaccine and is licensed to manufacture and market it. The attackers this time deployed Bookcode malware, which a security solutions company had previously found was linked to Lazarus in an attack on a supply chain through a South Korean software company. Kaspersky experts have previously found that the Lazarus Group distributed Bookcode malware through targeted phishing or through strategic attacks on websites.
Both wAgent and Bookcode malware used in both attacks have similar functionality; one of them is the full-function backdoor. After installing the last payload, the malware operator can take control of the victim’s machine in almost any way.
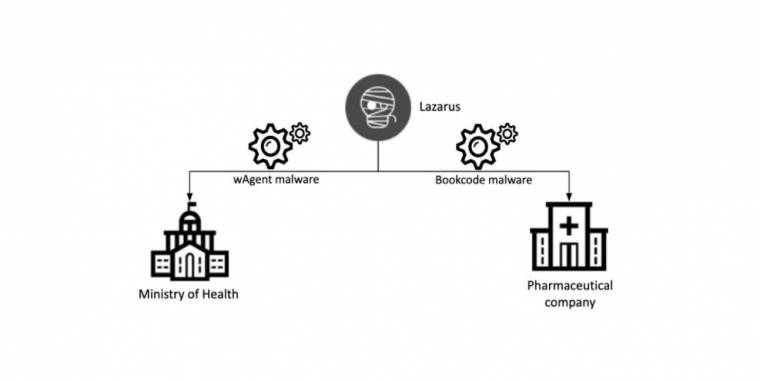
Connection diagram of the latest attack of the Lazarus group
In the light of the mentioned overlaps, Kaspersky experts According to him, it can be stated with great certainty that both incidents can be attributed to the Lazarus group. Experts will continue the investigation.
“These two incidents show that the Lazarus group is interested in information about COVID-19. Although the group is best known for its financial activities, this two cases are a good reminder that they may also be interested in strategic research. We believe that currently all vaccine research or crisis management organizations need to be fully alert to cyber attacks, “said Seongsu Park, a security expert at Kaspersky.
Kasperksy products detect wAgent malware as HEUR: Trojan.Win32.Manuscrypt.gen and Trojan.Win64.Manuscrypt.bx and Bookcode malware as Trojan.Win64.Manuscrypt.ce
Kaspersky recommends the following security measures to protect against sophisticated threats:
- The security operating system centers (SOC) teams and the latest threat analysis data. Kaspersky’s threat analysis portal provides access to data on the company’s threat analysis, including cyber-attack data and insights collected by Kaspersky over more than 20 years. Selected features of the service, which allow users to check files, URLs and IP addresses, are available free of charge here
- Provide employees with basic knowledge of cybersecurity, as many targeted attacks are triggered by phishing or other psychological manipulation techniques.
- For organizations that want to conduct their own tests, the company recommends the use of a tool called Kaspersky Threat Attribution Engine. The tool compares the detected malicious code with the malware databases and assigns it to the previously uncovered APT campaigns based on the similarities of the code.
- Use EDR solutions, such as Kaspersky Endpoint Detection and Response software, to provide endpoint-level protection against incidents, investigate them and remedy them in a timely manner.
- In addition to basic endpoint protection, a large enterprise-level security solution detects advanced network-level threats such as Kaspersky Anti Targeted Attack Platform at an early stage.
For more details on the new exploits documented above, read the full report on the Securelist website
The post Never enough: Kaspersky has uncovered two vaccine research-related APT incidents appeared first on World Weekly News.
