A phishing website can be put together in seconds
A cybercrime team has developed a new set of phishing tools that adapt to the victim, changing the logo and text of a disguised page that secretly engages in all sorts of “malice” in real time. A toolkit called LogoKit is already in full use by criminals, says security firm RiskIQ, which tracked the software’s career.
According to RisIQ, it has been in more than 300 domains last week and one in the past month. LogiKit has been installed in more than 700 locations. The tool tricks the victim into the site with phishing links and then imports your company logo from an external service. It uploads the victim’s email address in the email or username field, giving the target the appearance that they have logged in to the site at some point in the past. If you then enter your password unsuspectingly, LogoKit performs an AJAX search and sends the target email or password to an external address, then redirects the user to the actual corporate website.
LogoKit it does all this with embeddable JavaScript functions that can be added to any generic login form or HTML document. This solution differs from standard phishing toolkits, which mimic the authentication side of companies by pixels.
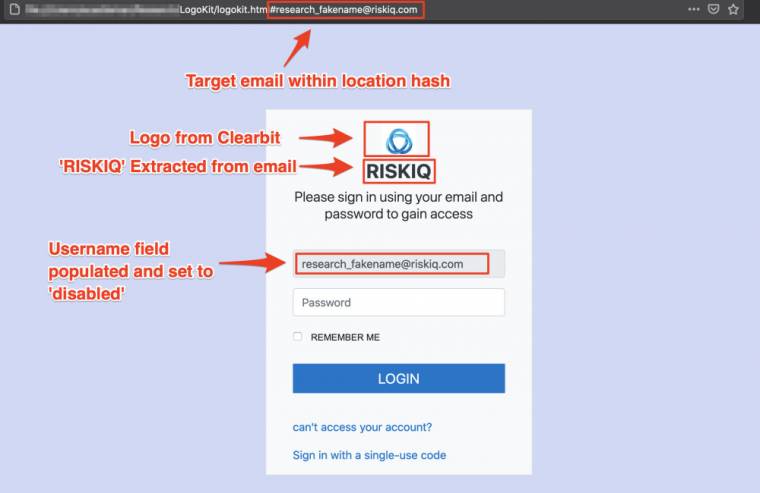
Due to the modularity of the toolkit, it can be used against any company and tens of thousands of criminals per week. they can carry out an attack with it. Due to its small size, it does not require a complicated server configuration and can be hosted from hacked sites or legitimate sites. Moreover, because it consists of JavaScript files, you can use trusted services such as Firebase, GitHub, and Oracle Cloud to host them, which are whitelisted in enterprise environments and are not followed by any alerts.
The post A phishing website can be put together in seconds appeared first on World Weekly News.
